Introduction
SSH tunnels provide a secure connection between two devices, using encryption to protect the data being transmitted. The authentication process used by SSH ensures that only authorized users can access the tunnel and the data being transmitted through it.
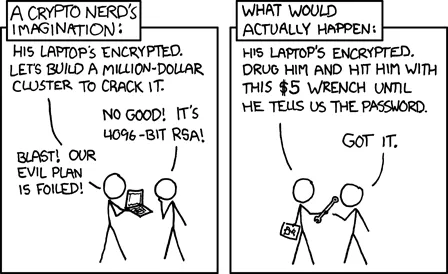
Theoretically, it is possible to brute-force and decrypt an SSH stream. However, by the time even the most powerful computer could decrypt the key, a solar explosion would have wiped out humanity and destroyed Earth.
🔑 For a 256-bit (ECDSA) key, there are 2^256 combinations
One hundred fifteen quattuorvigintillion, seven hundred ninety-two trevigintillion, eighty-nine duovigintillion, two hundred thirty-seven unvigintillion, three hundred sixteen vigintillion, one hundred ninety-five novemdecillion, four hundred twenty-three octodecillion, five hundred seventy septendecillion, nine hundred eighty-five sexdecillion, eight quindecillion, six hundred eighty-seven quattuordecillion, nine hundred seven tredecillion, eight hundred fifty-three duodecillion, two hundred sixty-nine undecillion, nine hundred eighty-four decillion, six hundred sixty-five nonillion, six hundred forty octillion, five hundred sixty-four septillion, thirty-nine sextillion, four hundred fifty-seven quintillion, five hundred eighty-four quadrillion, seven trillion, nine hundred thirteen billion, one hundred twenty-nine million, six hundred thirty-nine thousand, nine hundred thirty-six!
Can SSH tunnels be tracked?
The information exchange over an SSH connection with a server is secure and encrypted, so you would need to crack SSH to decipher what is being sent trough it. However, because the IP packets containing that communication cannot be encrypted, if you were to look at just one of them, you would be able to determine my location (source IP address) and the location of the SSH server (IP destination address).
The communication with the server through an SSH tunnel is just another TCP/IP conversation with a distant location. That connection is encrypted while it is traveling via the tunnel, but it is not encrypted after it exits the tunnel.
Only the IP destination address and the SSH server would be visible if you were to discover that second chat in the open (source IP address). It's unlikely there's anything special in those packets that shows SSH had anything to do with it; rather, there's not much (considering TCP/IP headers) to distinguish it from some other internet traffic that was generated on the SSH server computer.
This doesn't mean that the traffic couldn't be traced back to you; it just means that TCP/IP header analysis alone wouldn't be enough to do so.
Examples of malicious SSH usages
- Creating a reverse SSH tunnel to bypass a firewall or NAT and gain access to a protected network.
- Using an SSH tunnel to exfiltrate data from a target network, as the tunnel provides an encrypted connection that is less likely to be detected.
- Using an SSH tunnel to pivot from an initial foothold on a target network to other devices on the same network.
- Setting up an SSH honeypot to lure in potential attackers and gather intelligence on their tactics and techniques.
- Using an SSH server as a command and control (C2) server to remotely control malware or other malicious tools.
It's important to note that these are just a few examples, and hackers can use SSH in many other ways as part of an attack. It's important to take a comprehensive approach to security to protect against these and other threats.
When used correctly, SSH tunnels can be a safe and legal way to connect to a network or device remotely. Administrators often use SSH tunnels to connect securely to remote servers or devices, and it wouldn't be true to say that all uses of SSH tunnels are bad.
As with any tool, it's important to use SSH tunnels responsibly and follow best practices for securing your connection and preventing unauthorised access.
