What is an SSH tunnel?
An SSH tunnel consists of an encrypted tunnel created through an SSH protocol connection. Data transferred through the tunnel is encrypted, providing a secure connection between the two computers. SSH tunnels can be used to transfer data between computers, or to connect to a network resource that is not directly accessible from the internet.
What are the types of SSH tunnels?
Local forwarding allows you can use a local device to safely access a network resource on a remote network. Read more.
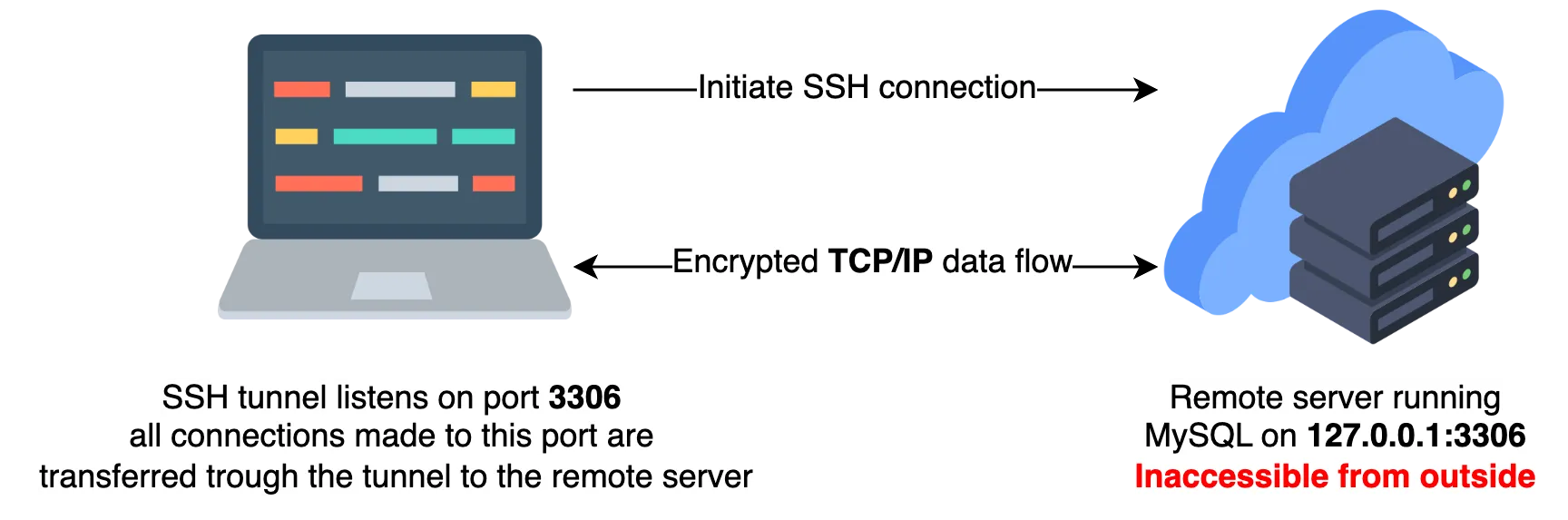
Remote forwarding is used to access a network resource on a local network securely from a device on the Internet. Read more.
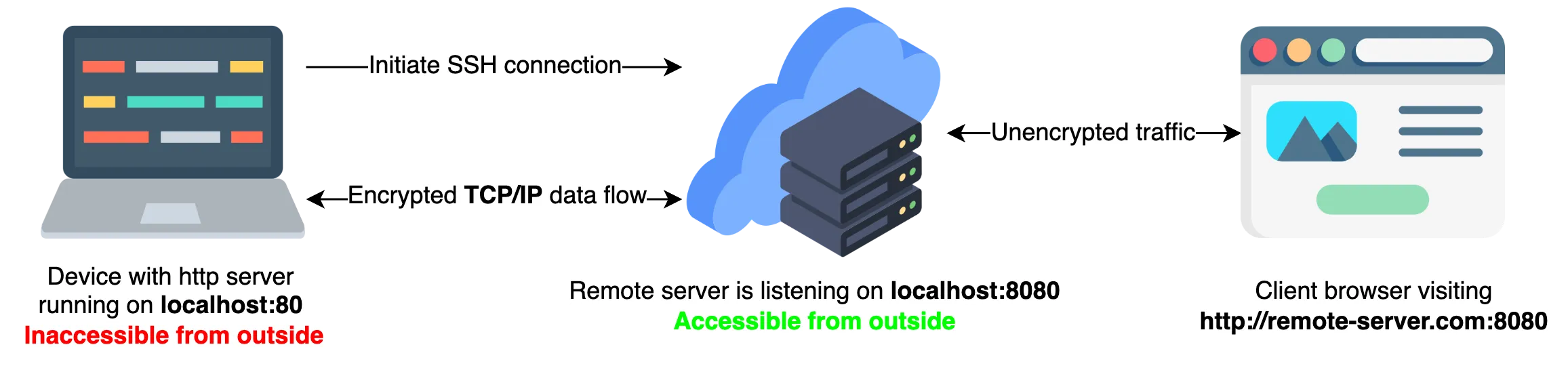
Dynamic port forwarding is useful when you want to connect to a remote network through a secure tunnel but don't know which ports on the remote network you need to access in advance. Read more.
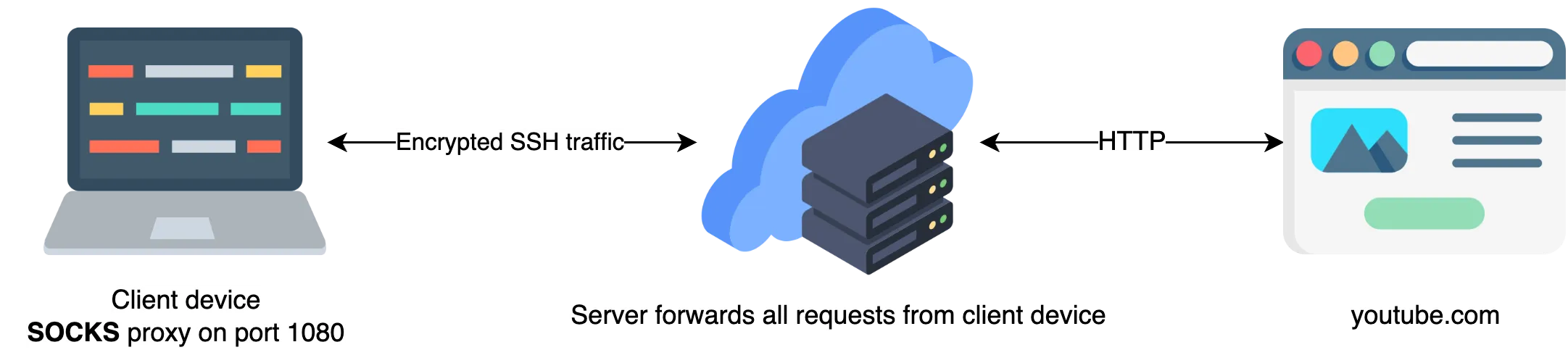
How does SSH tunnel work?
- You connect to the remote device using an SSH client on your local device.
- The SSH client establishes an encrypted connection with the remote device using SSH protocol.
- You can then use this encrypted connection to transfer data between your local device and the remote device.
One common use of SSH tunneling is to securely access a remote network or a network resource that is not directly accessible from the Internet. For example, you can use SSH tunneling to access a database or a web application running on a private network from a public network.
What are the most common use cases for SSH tunnels?
- Port forwarding: SSH tunneling can be used to forward a port on your local device to a port on a remote device. This allows you to access a service on the remote device as if it were running on your local device.
- Remote access: SSH tunneling can be used to securely access a remote network or a network resource that is not directly accessible from the Internet. For example, you can use SSH tunneling to access a database or a web application running on a private network from a public network.
- Secure file transfer: SSH tunneling can be used to securely transfer files between two devices over the Internet.
- Bypassing network restrictions or censorship: SSH tunneling can be used to bypass network restrictions or censorship. For example, you can use SSH tunneling to access blocked websites or services from a country where they are restricted.
- Network monitoring: SSH tunneling can be used to monitor network traffic and collect data for network analysis.
- Debugging: SSH tunneling can be used to debug network issues by creating a secure connection between two devices and capturing traffic between them.
If you want to find out more, we have plenty of articles covering SSH tunneling.
